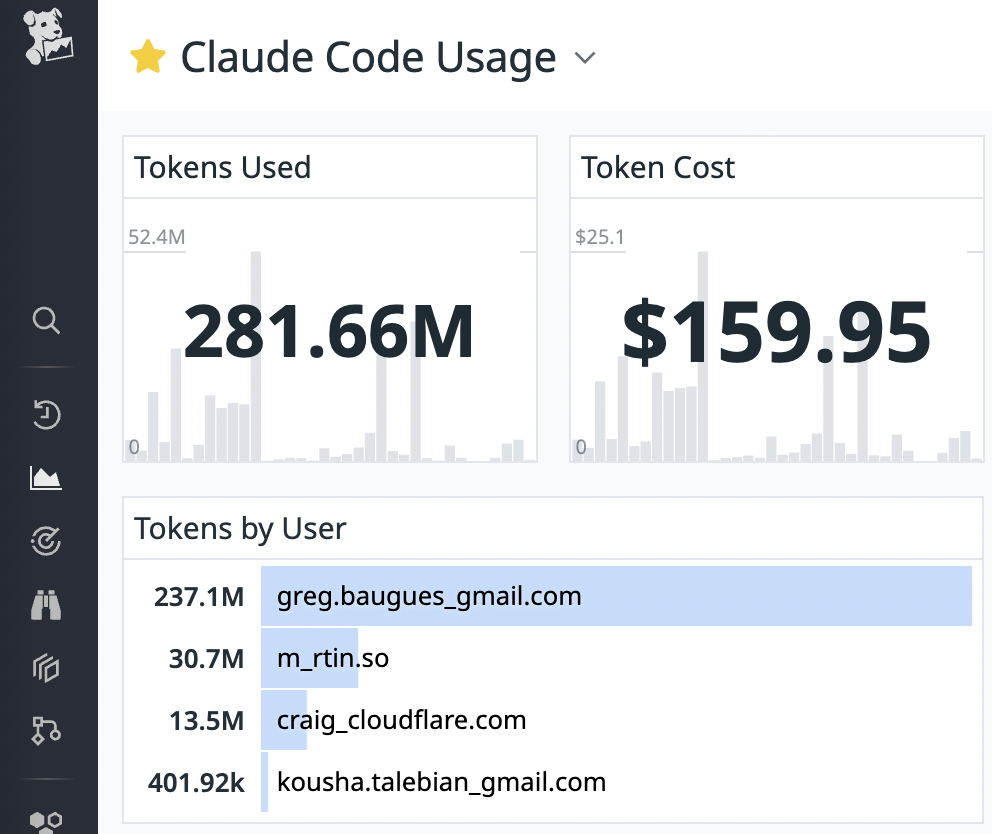
This week, I noticed a tweet announcing OpenTelemetry (OTel) support in Claude Code - Anthropic’s AI-powered coding assistant that lets you delegate tasks directly from your terminal. This new OTel integration allows you to stream token, session, and command metrics to any backend that speaks the OpenTelemetry Protocol (OTLP). Curiously, this feature hasn’t landed in the official changelog yet. Below, we’ll explore three different approaches to wiring Claude Code metrics into Datadog, the trade-offs between each method, and how to leverage these metrics effectively.